2011 in Review: Top Computer Hacks That Shook the World
This year saw a number of sensational instances when the Web sites of various government agencies and corporations were hacked, in what appeared to a series of cyber-wars, initiated by a group of hackers.
This may sound grim but 2011 was, in several ways, the Year of the Hackers, with damages rumored to be running to millions of dollars.
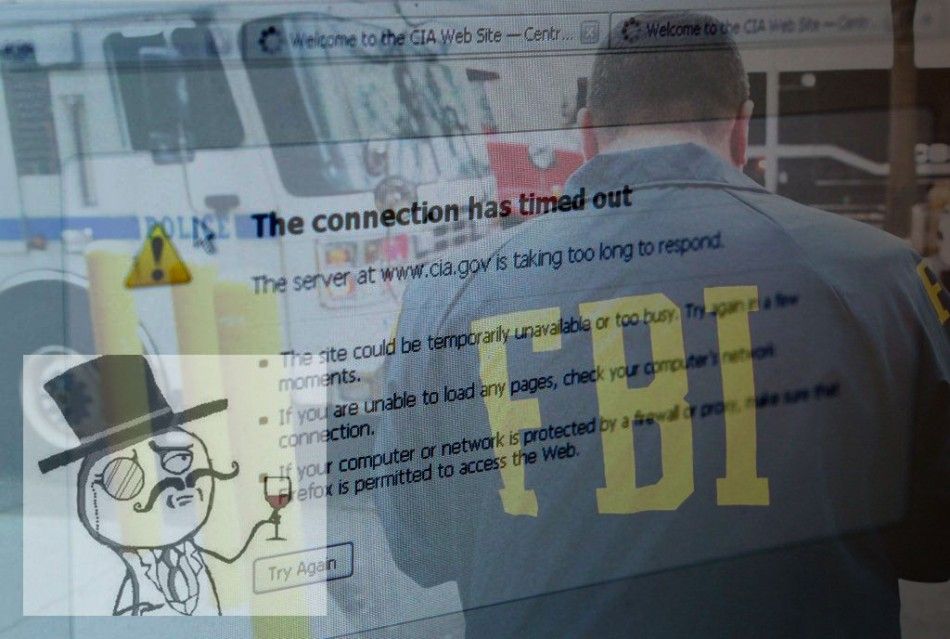
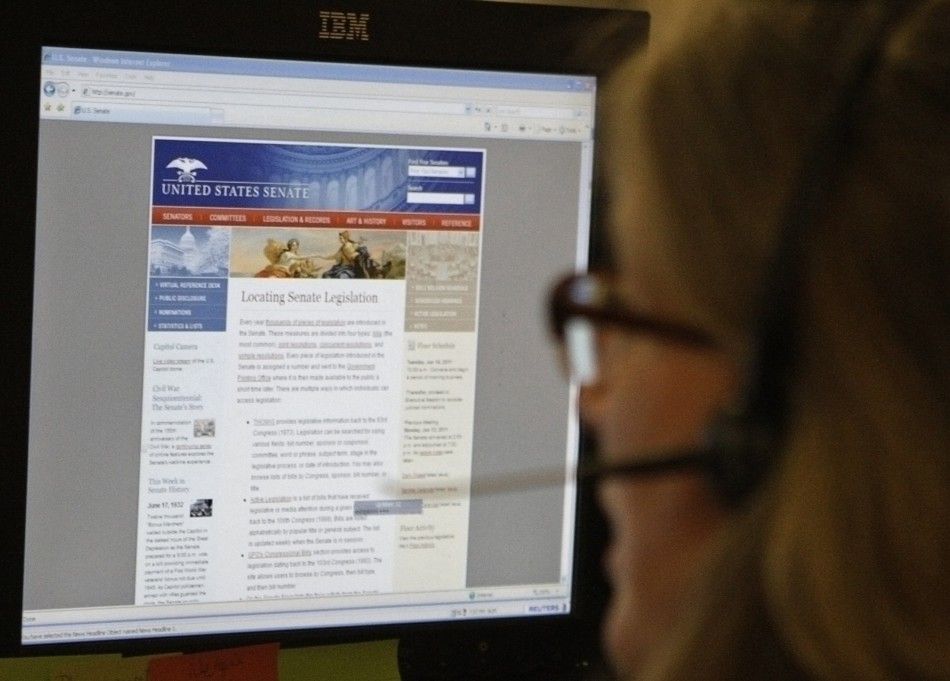
Hacker group Lulz Security (LulzSec) claimed responsibility for a number of large-scale data breaches and, working closely with another hacker collective called Anonymous, LulzSec encouraged other groups and individuals to open fire on any government or agency that crosses their path. They named the undertaking as Operation Anti-Security.
Check out the slideshow for more details on the most sensational hacks of 2011.








© Copyright IBTimes 2024. All rights reserved.












