Apple Quietly Responds To iOS Backdoor Allegations Through Knowledge Base Article

Amid allegations that Apple’s iOS has a number of suspicious software services that could be used to access user data, the Cupertino, California, tech titan quietly clarified their purposes and functions, which it claims are used for diagnostics.
In a knowledge base article published Wednesday, Apple Inc. (NASDAQ:AAPL) went over three software services built into iOS along with their roles and functions, stressing that each diagnostic function requires explicit permission from users by unlocking their iPhone or iOS device and trusting the computer via a dialog box.
An excerpt from the Apple support article:
“1. com.apple.mobile.pcapd
pcapd supports diagnostic packet capture from an iOS device to a trusted computer. This is useful for troubleshooting and diagnosing issues with apps on the device as well as enterprise VPN connections. You can find more information at developer.apple.com/library/ios/qa/qa1176.”
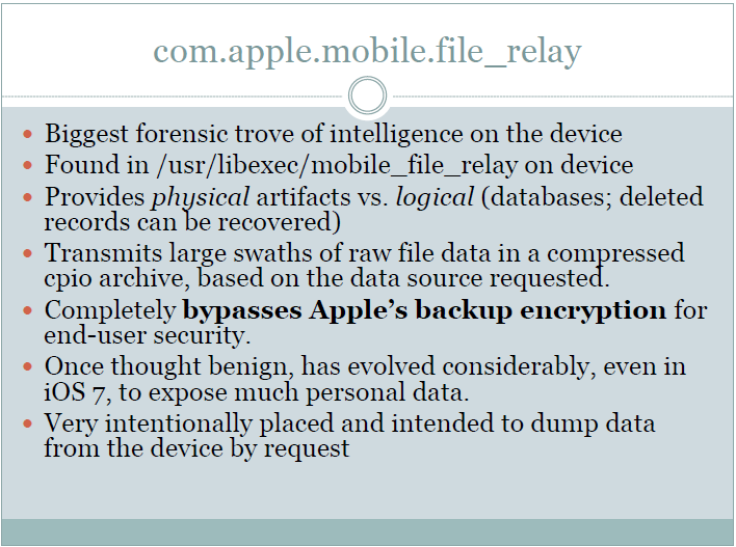
The knowledge base article proceeds to explain two more processes that were examined by Jonathan Zdziarski, the iOS security expert who first presented the previously undocumented services on July 18 at the HOPE/X Conference in New York.
Zdziarski noted in his presentation that the services in question could be used and exploited by law enforcement or other entities to extract data from Apple iPhones and devices running iOS. But he also clarified that he wasn’t accusing Apple of working with government entities such as the National Security Agency.
While Zdziarski gave Apple some credit for acknowledging the existence of such services, he was quick to fire back Wednesday, alleging that Apple was downplaying the severity of the diagnostic services’ functions.
“I give Apple credit for acknowledging these services, and at least trying to give an answer to people who want to know why these services are there -- prior to this, there was no documentation about file relay whatsoever, or its 44 data services to copy off personal data. They appear to be misleading about its capabilities, however, in downplaying them, and this concerns me,” Zdziarski said in a blog entry.
Addressing each service individually, Zdziarski took issue with how they were implemented.
“The problem I have with its implementation, however,” Zdziarski wrote. “In iOS, pcapd is available on every iOS device out there, and can be activated on any device without the user’s knowledge.”
He went on to criticize two additional services, File Relay and House Arrest, which purportedly have the ability to access personal data and information without user permission.
Apple responded Monday to an inquiry by Financial Times reporter Tim Bradshaw about Zdziarski’s allegations in his July 18 presentation.
Apple statement denies working with "any government agency ... to create a backdoor in any of our products" pic.twitter.com/5psXWtOXW2
- Tim Bradshaw (@tim) July 21, 2014“As we have said before, Apple has never worked with any government agency from any country to create a backdoor in any of our products of services,” Apple said to Bradshaw.
It’s unknown if Apple plans to patch the services questioned by Zdziarski, but he hopes that something that will be done to fix the issues raised by his presentation.
“It would be wildly irresponsible for Apple not to address these issues, especially now that the public knows about them,” Zdziarski wrote.
© Copyright IBTimes 2024. All rights reserved.












