FinFisher: Malicious Spyware Disguised As Mozilla Firefox Discovered In 36 Countries
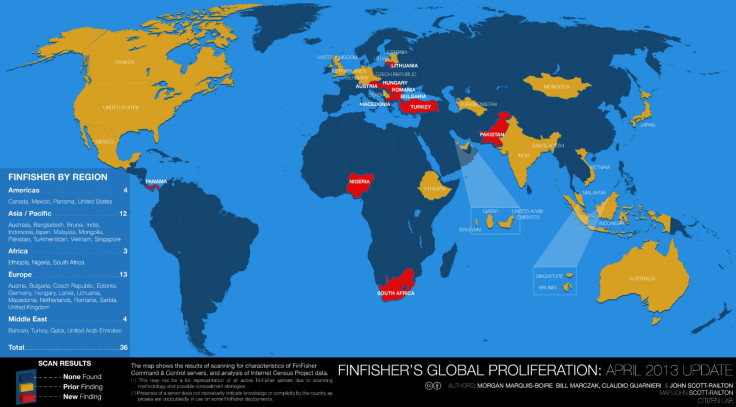
A new report from Citizen Lab shows 36 countries actively using FinFisher (aka FinSpy), a sophisticated malware that infiltrates computers to grab screenshots, record chat conversations, log keystrokes and even hijack the camera and microphone. Previously used to spy on pro-democracy activists in Bahrain, the spyware is now tricking users into thinking it is Mozilla’s Firefox Web browser.
Mozilla announced on its blog Tuesday that it sent a cease-and-desist letter to Gamma International, a UK company that sells surveillance software to governments for illegally using the Mozilla brand. The spyware is named Firefox.exe and includes properties associated with Firefox, including version number and copyright claims attributed to “Firefox and Mozilla Developers.” Expert users have also found that the underlying code of the FinFisher spyware matches verbatim the assembly manifest of Firefox.
While the FinFisher spyware doesn’t compromise a user’s browser, the disguise prevents it from being detected and deleted.
Citizen Lab, a research group at the University of Toronto dedicated to the intersection of digital media, global security and human rights, also reported that the spyware is targeting Malay-language speakers. Another version of FinFisher is disguised as a document discussing Malaysia’s upcoming 2013 election.
Even the United States recently got a look at how governments want to use Gamma’s spyware. A court rejection revealed an FBI plot to infect an anonymous computer with malware and convert the webcam into a surveillance camera to track a suspected criminal. It was suspected that the FBI purchased this software from Gamma International.
The FinFisher spyware is specifically engineered to elude antivirus software made by Kaspersky Lab, Symantec, F-Secure and others. There are also mobile versions of FinFisher designed specially to attack major mobile phones.
In addition to the U.S., Bahrain and Malaysia, Citizen Lab identified servers hosting FinFisher in a host of countries, including Australia, Austria, Bangladesh, Brunei, Bulgaria, Canada, Czech Republic, Estonia, Ethiopia, Germany, Hungary, India, Indonesia, Japan, Latvia, Lithuania, Macedonia, Mexico, Mongolia, Netherlands, Nigeria, Pakistan, Panama, Qatar, Romania, Serbia, Singapore, South Africa, Turkey, Turkmenistan, United Arab Emirates, the United Kingdom and Vietnam. These servers were identified in the report as “command-and-control” servers, which are often used by cyber criminals to operate botnets installed by malware.
© Copyright IBTimes 2024. All rights reserved.












