How To Make Sure You Don't Fall For An iOS Phishing Attack

Apple has a habit of regularly prompting users to enter their iTunes Store password while using apps and services on their iOS device. While the practice may seem like an extra step of security, a mobile developer believes it is actually inviting hackers to steal login credentials.
Felix Krause, an iOS developer and the creator of the app creation automation tool Fastlane, warned that it is incredibly easy to create a spoofed version of Apple’s login screen designed to harvest the username and password of unsuspecting victims who mindlessly enter their password like any other time they see the prompt.
In a proof of concept attack that Krause concocted, he showed that an attacker could easily create a faux version of Apple’s login screen popup and use it to record the login information of iOS users.
According to Krause, because the login screen is already such a common sight for most users that the average person wouldn’t question seeing it pop up while browsing the web or in the middle of using an application. By inserting the login prompt into an otherwise innocuous-seeming app or on a website, an attacker could easily launch a phishing attack for iOS credentials.
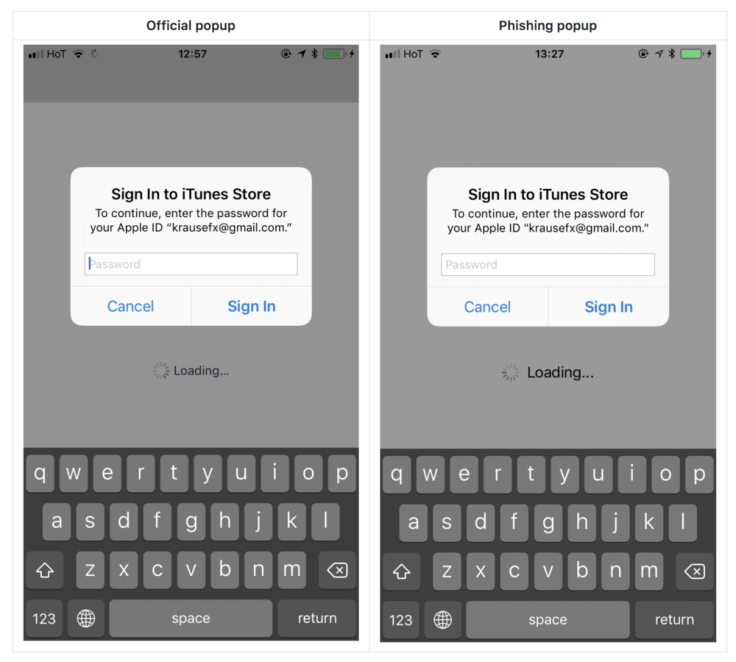
In researching the attack Krause found that users aren’t always shown their email address when they are prompted for their password, which further lowers the bar for an attacker as they do not have to present the user’s email in order to obtain their password.
Krause also warned that users who have two-factor authentication enabled on their devices may be able to protect their iTunes and iCloud account from being compromised, but still run the risk of other accounts linked to the same email address being attacked. Because many people use the same password for multiple accounts, hackers are likely to try to login using the stolen username and password on other services.
While the developer recommends a number of solutions for Apple to take in order to counteract such an attack, including creating distinct differences between the system’s user interface and an app’s user interface to tip off users to an official prompt and a fake one.
He also advised that Apple direct users to the Settings app to login rather than allowing it directly through a notification pop up. The change would create a slight inconvenience to users, but security often comes with compromises.
Those are fixes for Apple to take on at some point in the future, but for the time being it is up to users to use caution and protect themselves to avoid falling victim to such a scam.
The first thing an iOS user can do to make sure they are dealing with a legitimate login request is simply hit the home button on their device. If the app closes and the dialog box disappears, the prompt was likely fake. If the login screen remains, it’s a system dialog box and it is safe to enter a password. System dialogs operate differently than those that are part of an app and hitting the home button is the quickest way to spot the difference.
Users can also dismiss the dialog box entirely and go directly to their Settings app to enter their password manually. The method leans on a concept recommended for avoiding phishing emails; never click directly on a link, always visit the website asking for your information by entering the address yourself to ensure it is valid.
© Copyright IBTimes 2024. All rights reserved.











