Is Your Mac Secure? No Password Needed For Admin Privileges On macOS High Sierra Bug

A recently discovered security vulnerability in Apple’s latest version of its MacOS operating system allows anyone to gain administrative access to the machine without entering a password.
The issue was first discovered by software developer Lemi Ergin and appears to plague MacOS High Sierra. For affected machines, a person can login to the administrator account by simply entering “root” as the username with no password.
The vulnerability allows any person to access the administrator’s account on an already unlocked Mac. It can also be used at the login screen of a locked Mac to unlock the machine and gain full administrative access.
The vulnerability does not always work on the first attempt, but simply continuing to click the “Unlock” button with “root” entered as the username and no password provided will eventually unlock the machine.
International Business Times was able to successfully replicate the issue on a MacBook Air and a MacBook Pro, both running version 10.13.1 of MacOS High Sierra. It also appears to be active in the beta version of MacOS 10.13.2. A GIF of the bug in action can be seen below:
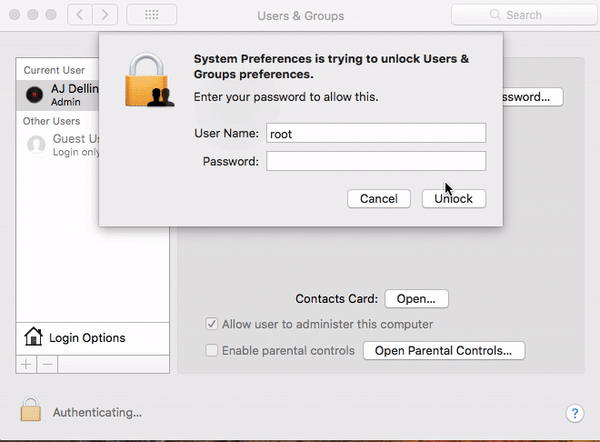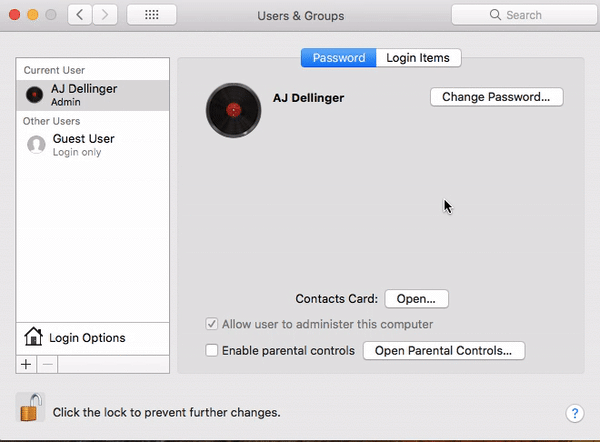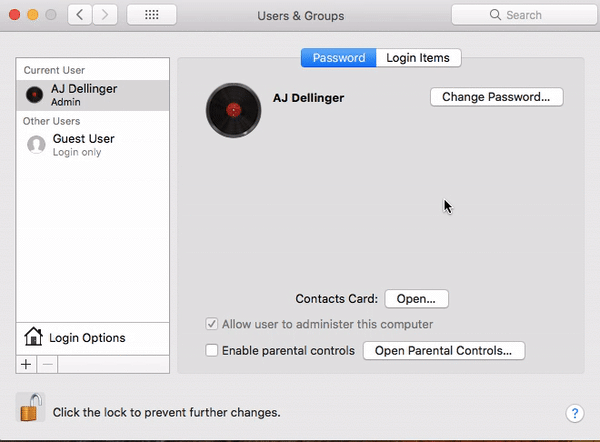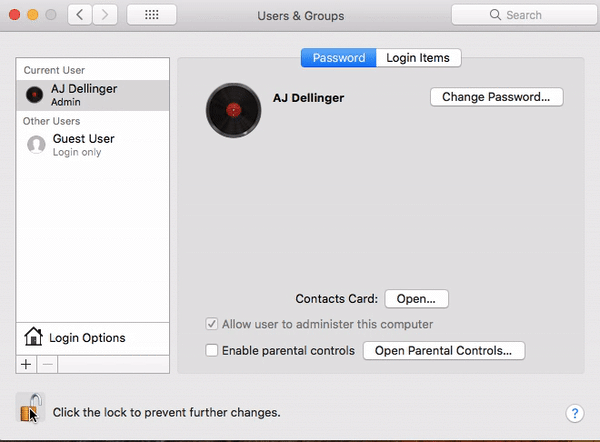
Mac users can replicate the issue to see if they are affected with the following steps:
Open System Preferences and click on the “Users & Groups” menu. Click on the lock in the lower left of the menu to make changes. A login prompt will appear. Enter “root” as the username and leave the password field empty. Click on the “Unlock” button. If the lock is unlocked, the machine is affected by the security flaw.
Ben Johnson, the chief technology officer of Obsidian Security and a former U.S. National Security Agency computer scientist, described the flaw to IBT as "a hacker's dream." He said the "only silver lining" about the bug is that it requires local access to the system and does not appear to be exploitable remotely. "Still, anyone with a Mac needs to keep an eye on soon forthcoming updates and patches," he said.
A number of users have reported the issue is not active in other versions of MacOS. Those running previous versions of MacOS including Sierra and Yosemite do not appear to be affected by the bug. Alasdair Allan, a consultant and hacker, confirmed on Twitter that MacOS Sierra (10.12) is not affected by the issue.
IBT reached out to Apple for comment regarding the discovery of the security vulnerability. The company has issued a statement saying, "We are working on a software update to address the issue. In the meantime, setting a root password prevents unauthorized access to your Mac."
maxOS High Sierra Bug: How To Fix The Root Access
Currently, there is no official fix from Apple regarding the issue. However, there is a workaround that will provide users with some additional security to prevent against unauthorized logins: users can enable a root account that requires a password to gain access.
To do so, open the System Preferences and click on the “Users & Groups” option. Click the lock to make changes and enter the administrator name and password. Click “Login Options,” then click “Join,” which appears next to the text “Network Account Server.”
Once in the “Join” menu, click on “Open Directory Utility.” When the next menu appears, click the lock in the lower left to make changes. Enter the administrator name and password. Then from the menu bar at the top of the screen, click on the “Edit” menu and choose “Enable Root User.” This will prompt for a password for the Root user account.
Once a password has been set for the “root” account, the flaw that allows a person to login as “root” with no password will no longer work.
© Copyright IBTimes 2024. All rights reserved.











