Adult Player Porn App Takes Pictures Of Users And Demands Ransom

Just as there is no such thing as a free lunch, in the digital world, a good rule of thumb to follow is that there is no such thing as free pornography. Whether you pay using your credit card or by looking at ads, you do have to pay and users of an Android app promising free porn have found that out to their cost.
Adult Player advertises itself as a free porn video app for Android smartphones and tablets but is, in fact, a piece of ransomware. The app takes pictures of users while they use it before locking the device and demanding a $500 ransom for access to the phone. The app is downloaded from unofficial sources and is not available on the Google Play store.
Upon installation Adult Player, which was discovered by security researchers at Zscaler, requires permissions including administrator access that allow it to surreptitiously install malicious files. It then checks if the device has a front-facing camera and, once the app is launched, begins silently taking pictures of the user.
These pictures are then used to generate a customized warning page that the ransomware displays, demanding a ransom of $500 to unlock your device, which it wants routed through PayPal. The malware also sends details about the device to a remote server, including device type and operating system.
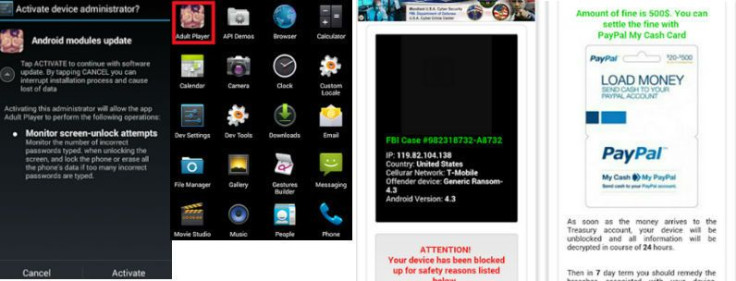
The warning screens say the device has been locked "for safety reasons" and claims to be a warning from the FBI for visiting "forbidden pornographic sites." The message also lists the location, the operator and the version of the Android software running on the phone. The ransomware is designed to be persistent so even if the device is rebooted the message remains on the screen until the ransom is paid.
This is far from the first app that has promised something for free but typically costs the user, and the fact that apps can be installed on Android devices from sources other than Google Play means the issue is likely to continue.
While a normal reboot doesn't work, Zscaler has the following advice on how to remove such an app:
- Boot device into safe mode (Please note that entering "safe mode" varies depending on your device). Safe mode boots the device with default settings without running third party apps.
- Uninstalling ransomware from device requires you to first remove administrator privilege. To do the same, go to Settings --> Security --> Device Administrator and select ransomware app, then deactivate.
- Once this is done, you can go to Settings --> Apps --> Uninstall ransomware app.
© Copyright IBTimes 2024. All rights reserved.












