A critical funding shortfall imperils internet access for low-income Americans, prompting urgent calls for congressional action to avert a looming crisis.
Here, we have compiled 15 YouTube Shorts with the most likes.
FCC bans AI-generated robocalls to protect consumers from scams and misinformation, emphasizing its commitment to safeguarding telecommunications integrity.
This guide delves into the world beyond NordVPN, highlighting the best VPN service providers for 2024 that deserve your attention.
If you're looking to upgrade your office Wi-Fi experience, these mesh Wi-Fi systems are your best options.
Discover the top 8 VPN services of 2023 that offer robust online privacy and security, ensuring your digital activities remain private and protected.
Explore the top six digital marketing agencies that excel in delivering unparalleled on-page optimization for enhanced online visibility and performance.
Discover the leading SEO service agencies in the U.S. that can elevate your online ranking to new heights.
Lebron James' media advisor said the NBA star did not pay for verification.
"It's only speculative. Obviously, that's really dangerous," the WWW inventor said when asked about cryptocurrency.
The federal judge clarified the hearing was not held to revoke Bankman-Fried's bail but he did not discount the possibility, saying "it could get there, conceivably."
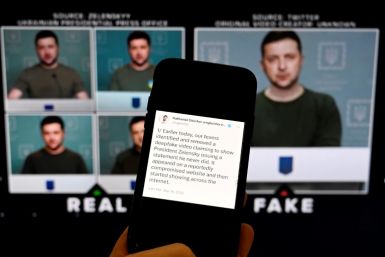
Seeing is believing? Global scramble to tackle deepfakes
Many people don't realize that they are committing some mistakes that are slowing down their Wi-Fi.
The Android banking malware was first discovered by Group-IB analysts, who think it is the heir of Anubis.
North Korean hackers have stolen non-fungible tokens (NFT) worth thousands of dollars, a blockchain security firm reported.
Party.Space metaverse events offer a 3D environment + video communication + game mechanics to ensure participants will not only have an unforgettable moment but also a very engaging online experience.
Wi-Fi 7 is the upcoming seventh generation of Wi-Fi technology, which promises to provide faster speeds and be more efficient than previous generations.
As for its other purpose, Nestorov shared that the Skif satellite would be involved in studying the "effects of space radiation, experienced by a satellite with the orbit of some 8,000 km above the ground."
The massive anti-Starlink radar was reportedly developed by the 14th Research Institute of China Electronics Technology Group Corporation.
So far, it is not yet clear how Twitter plans to verify the identity of the users but Musk said "there will be a secondary tag below the name for someone who is a public figure, which is already the case for politicians."
Vice Prime Minister Mykhailo Fedorov confirmed a few days ago at the Lisbon Web Summit that the Ukrainian government already had a discussion with SpaceX CEO Elon Musk about Starlink's service and expressed his confidence that the satellite internet service will continue in the country.
"Even though Starlink is still losing money & other companies are getting billions of taxpayer $, we'll just keep funding Ukraine govt for free," Musk said.
This vulnerability among secure instant messenger apps that can pinpoint users' location with 80% accuracy depending on the success rate of a "specially crafted timing attack."
Over the past two years, Todd Humphreys and his team at the University of Texas Austin Radionavigation Lab, have been reverse-engineering signals from Starlink internet satellites in low earth orbit (LEO) to ground-based receivers.
The Penatgon suggested on Friday that it is reviewing its options.
"I'm proud that we were able to provide the terminals to folks in Ukraine. It's been enormously helpful, I think, to ensure people are still communicating," Starlink president said in March.
"These apps were listed on the Google Play Store and Apple's App Store and disguised as photo editors, games, VPN services, business apps and other utilities to trick people into downloading them," Facebook disclosed.
This article discusses the 5 best legal ways to get free internet access at home.
The Utah State Representative's Twitter account was apparently hacked on Sept. 23.
The IT Army of Ukraine, over the past months, has shown its unyielding and steadfast commitment to fight for Ukraine and has by far maintained being a devastating force against Russia.