New Android Virus Forwards Text Messages To Hackers

A new Trojan malware infecting Android phones is capable of intercepting inbound text messages and forwarding them to hackers. The malware, called Android.Pincer.2.origin, is particularly troubling because it can easily thwart the two-step verification systems employed by online banking, email and social media accounts.
The malware, discovered by Russian antivirus company Doctor Web, spreads as a fake security certificate that tricks users into thinking they need to install it on their Android phones. After installation, users will get a notification that installation was successful, but the malware won’t do any other noticeable activities. It will instead run in the background, connecting to a remote server to send information about the user's Android device, including model and serial number, carrier information, phone number and operating system.
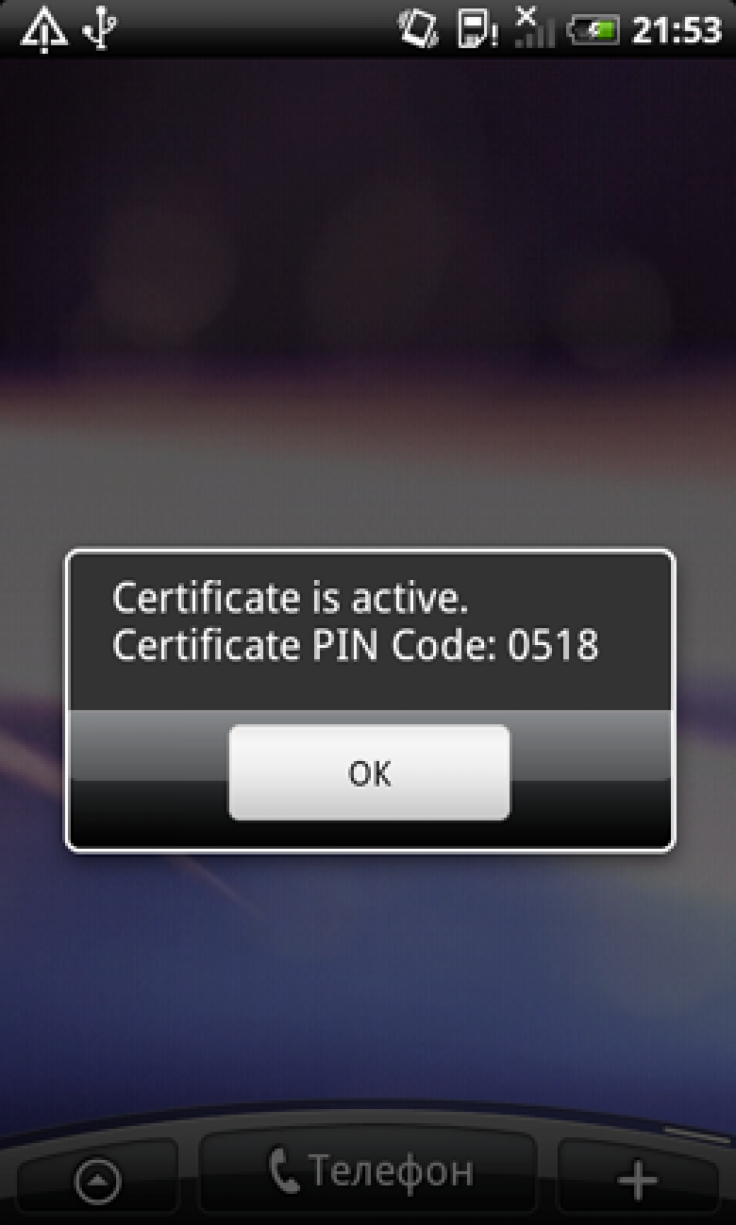
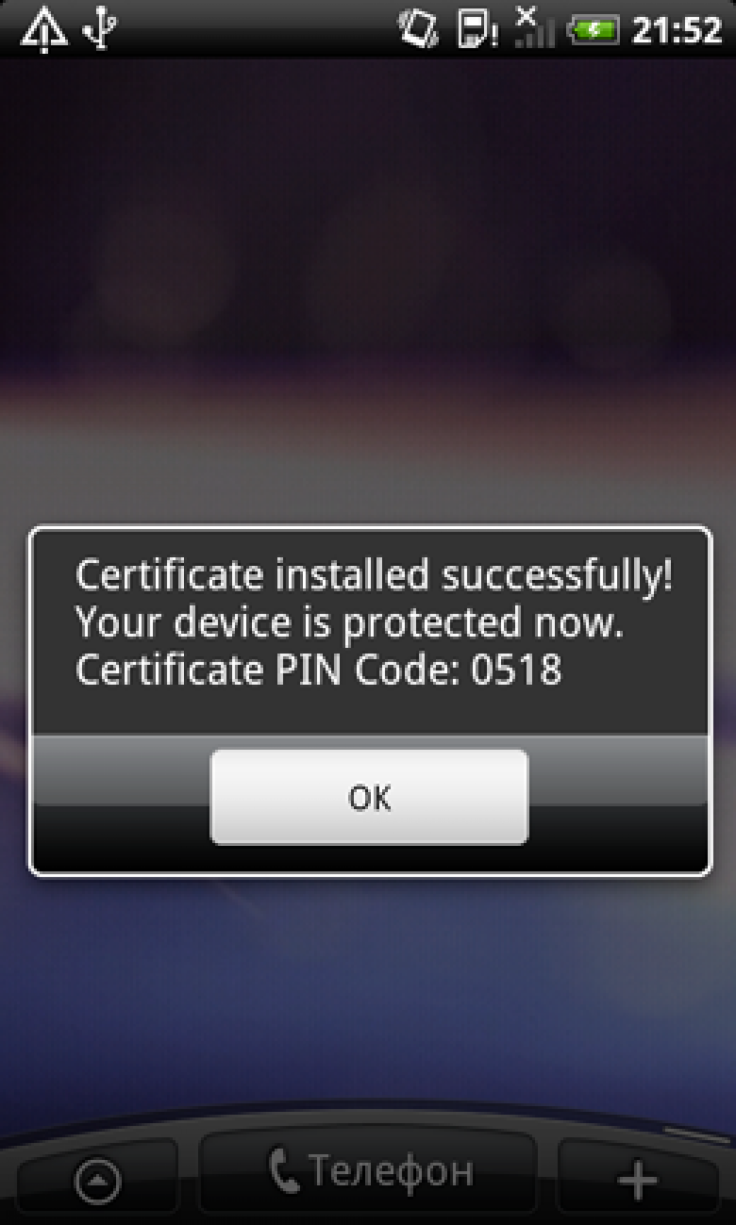
Once connected, hackers can send the malware instructions to intercept and forward messages from specific phone numbers, send new text messages, display a message on the Android device’s screen, and other deceptive activities.
The ability to specify a phone number from which to intercept messages allows a hacker to use the malware for targeted attacks, stealing only specific messages that contain valuable information. For example, the hacker could set the malware to forward texts received from banking services.
Two-step verification systems often use cellphone messaging to verify a user’s identity. The user registers his or her phone number with the service, and when they attempt to log in to their account, the service sends a text message with the password. The user must then use this password to complete the login.
The system, which Kim Dotcom claimed Thursday to have invented, is designed to protect against phishing scams that use malware to send hackers the login information. When an account requires a second password that is randomized each time and sent to a device that only the user has access to, not even a hacker with access to the primary user name and password can access it. Twitter announced a two-step verification system on Wednesday after hackers compromised several high-profile Twitter accounts.
But if a hacker has access to cellphone messages and can set the malware to forward every message sent from Twitter or a bank, they could get that password and access to the account. Stay on the lookout and be careful to install software only from trusted sources.
© Copyright IBTimes 2024. All rights reserved.












