Researchers Use ‘Quantum Data Locking’ To Create World’s First Quantum Enigma Machine
In 2013, Seth Lloyd, a professor of quantum information at Massachusetts Institute of Technology, put forward the idea of creating a "quantum enigma machine" — one that would be modeled after the World War II-era cipher machines but would use quantum states of photons to encode and encrypt messages.
Now, a team of researchers — led by Daniel Lum, a graduate student at the University of Rochester, and John Howell, a professor of physics at the university — have taken a step toward realizing this vision by actually demonstrating that an unbreakable encrypted message can be sent with a key that’s far shorter than the message.
This experiment, described in a new study published in the journal Physical Review A, violates what has hitherto been considered a fundamental rule of cryptography — that a randomly generated key being used to encrypt a message needs to be at least as long as the message itself. It does so through a technique the researchers call “quantum data locking.”
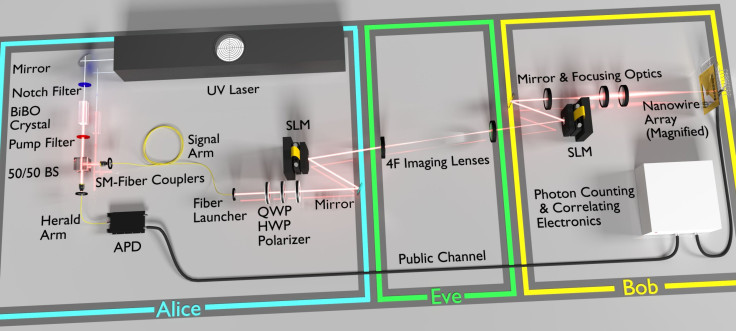
The quantum enigma machine developed by the researchers consists of three parts — a machine that generates photons, a spatial light modulator (SLM) that alters the amplitude and tilt of individual photons and also scrambles its wavefront, and an 8 by 8 photon detecting nanowire array.
Once a message is encrypted in such a way and transmitted, only those who have access to a previously agreed upon key can unscramble the message.
And, even if someone does manage to intercept the message, the very act of trying to unscramble it would result in it being corrupted. This is because of a unique property of subatomic particles wherein measuring its state actually changes it.
“Along with modifying the shape of the photons, Lum and the team made use of the uncertainty principle, which states that the more we know about one property of a particle, the less we know about another of its properties. Because of that, the researchers were able to securely lock in six bits of classical information using only one bit of an encryption key—an operation called data locking,” the researchers said in a statement.
Moreover, each photon in the experiment was encrypted with six bits of information, of which 2.3 bits were used to encode a secret key. As a result, by using a stream of 63 photons, they were successfully able to use just 145 bits to encrypt the entire packet of information.
“While our device is not 100 percent secure, due to photon loss, it does show that data locking in message encryption is far more than a theory,” Lum said. “Regardless, the field is still in its infancy with a great deal more research needed.”
© Copyright IBTimes 2025. All rights reserved.





















