Russians Hack Johns Hopkins Coronavirus Map To Steal User Information

KEY POINTS
- The hugely popular Johns Hopkins University COVID-19 interactive map has been hacked by Russian cybercriminals
- They're selling copies of the interactive map as part of a malware tool that steals passwords and user data
- The U.S. warns everyone not to open attachments or links to fraudulent websites
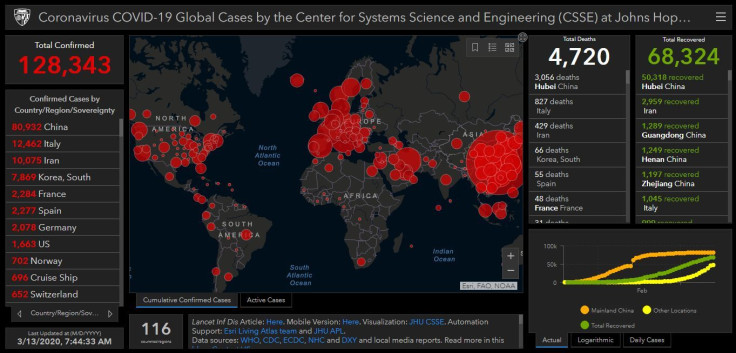
The constantly updated data about the casualty toll inflicted worldwide by COVID-19 placed online by the Center for Systems Science and Engineering (CSSE) at Johns Hopkins University is an invaluable tool in saving lives.
Unfortunately, some people see this humanitarian endeavor as a means to hack into the computers of those using the CSSE website and make dirty money in the process. Russian cybercriminals are selling to other cyber crooks a digital coronavirus infection kit that uses the CSSE interactive map as part of a Java-based malware deployment scheme, warns Brian Krebs, the American journalist and investigative reporter best known for his coverage of profit-seeking cybercriminals.
This malware interactive map, which looks like the real thing, is sent as an attachment to a victim. Clicking on the interactive map (which is in reality a malware PreLoader), will either deploy password-stealing malware or send itself to the victim's email list. Krebs also believes the CSSE interactive map is also being used as attachments to spam e-mails.
He said a member of several Russian language cybercrime forums in late February began selling a digital coronavirus infection kit that uses the CSSE interactive map as part of a Java-based malware deployment scheme. According to Krebs, the kit loads a fully working online map of coronavirus infected areas and other data. The malware map is resizable, interactive, and has real time data from World Health Organization and other sources.
"Users will think that PreLoader is actually a map, so they will open it and will spread it to their friends and it goes viral!” the seller of the malware says in a video explaining the exploit.
What makes this Java-based map more dangerous is that it can apparently be bundled into a filename most webmail providers allow in sent messages. The source said the user/victim, however, has to have Java installed for the map and exploit to work. He also makes the astounding claim the map will work even on fully patched versions of Java.
“Loader loads .jar files which has real working interactive Coronavirus realtime data map and a payload (can be a separate loader),” said the seller. “Loader can predownload only map and payload will be loaded after the map is launched to show map faster to users. Or vice versa payload can be predownloaded and launched first.”
This new malware kit seems to be drawing a lot of interest among cybercriminals given the dominating presence of news about the COVID-19 pandemic on the internet these days. Earlier this week, cybersecurity experts began warning of new malicious websites using interactive versions of the same map to distract visitors while the sites tried to infiltrate the password-stealing AZORult malware.
Online scams and malware linked to COVID-19 has become so prevalent the U.S. Department of Homeland Security (DHS) is warning individuals to remain vigilant. The DHS' Cybersecurity and Infrastructure Security Agency (CISA) warns that cybercriminals are sending emails with malicious attachments or links to fraudulent websites to trick victims into revealing sensitive information or donating to fraudulent charities or causes.
It said people must "exercise caution in handling any email with a COVID-19-related subject line, attachment, or hyperlink, and be wary of social media pleas, texts, or calls related to COVID-19." CISA also warns people not to reveal personal or financial information in email, and not to respond to email solicitations for this information.
© Copyright IBTimes 2025. All rights reserved.





















