iPhone Malware YiSpecter Spread By Chinese Advertising Company Highlights Apple's Growing Security Problem

LONDON -- The view that Apple’s iOS is a malware-free zone is quickly eroding as the latest piece of malicious software targeting iPhone and and iPad users highlights a growing problem for a platform once dubbed “the security innovation of the decade.”
Within a month of the discovery of the XcodeGhost malware affecting thousands of iOS apps and hundreds of millions of users, researchers have discovered YiSpecter, a piece of malware which disguises itself as a free porn app, has been in the wild for at least 10 months, users four different methods of infecting victims’ devices.
XcodeGhost was seen as the first major breach of Apple’s typically tight App Store security and came 10 months after the discovery of WireLurker which targeted both Apple’s mobile and desktop users.
Most iOS malware to date has targeted jailbroken devices, but YiSpecter, reportedly developed by a Chinese mobile advertising company, affects non-jailbroken devices too. The malware also has built-in persistence meaning that even if you manually delete the malware, it will automatically re-appear. Along with the unique methods of distributing the malware, the authors of YiSpecter also “abuses private APIs in the iOS system to implement malicious functionalities.”
Private APIs are programming functions Apple does not make public as they are not though to be stable, meaning the way they work could change in the future or they may disappear altogether.
Apple typically rejects apps which invoke Private APIs but research due to be presented at the ACM Conference on Computer and Communications Security next week claims that more than 100 apps currently available in the App Store abuse this function.
Abusing Private APIs
Researchers from Purdue University claim to have discovered 146 iOS apps from the App Store that abused 150 different private APIs including 25 APIs that are security critical -- occupying about 7 percent of all apps they analyzed. The researchers even found a third-party advertisement library that abused private APIs to collect private user information.

“Our results show that, contrary to popular belief, a nontrivial number of iOS applications that violate Apple’s terms of service exist in the App Store,” the researchers said.
Commenting on the research from Purdue University, Claud Xiao, the researcher from Palo Alto Networks who uncovered the YiSpecter malware, said: “As a community, many of us [security researchers] have considered Apple’s code review on private APIs good enough and that abusing private APIs can only be successful if combined with enterprise distribution -- like in the case of the YiSpecter. Through this research, we now know that abusing private APIs in the iOS system could be an independent attack technique and could affect all iOS users.”
YiSpecter is currently affecting users in China and Taiwan, but its discovery “pushes the line barrier of iOS security back another step,” according to Xiao. The rise in high-profile malware attacks against iOS have predominantly come from China during the last 12 months, which is unsurprising considering the huge number of iPhones the company is selling in the country, a figure boosted with a deal with the world’s largest mobile phone network China Mobile last year.
However, as the research from Purdue University shows, the abuse of Private APIs is not limited to China and could present a potentially huge problem for Apple says Xiao: "What [the report] means is the attacking technique of abusing private APIs can also be used separately and can affect all normal iOS users who only download apps from the App Store.”
This opinion is also held by Mark James from security firm Eset: "We are seeing more and more instances of malware affecting non-jailbroken iPhones and that has to ring a few alarm bells. Currently the YiSpecter malware is affecting mainland China and Taiwan but we will see some strains and variants making its way into the rest of the world."
Free Porn App
In the case of YiSpecter, users are tricked into installing the malware as it is disguised as a video app which allows users to watch pornographic videos for free, allowing them access more content if they download additional apps. Once an iPhone or iPad has been infected with YiSpecter, the malware can download, install and launch arbitrary iOS apps, replace existing apps with those it downloads, hijack other apps’ execution to display advertisements, change Safari’s default search engine, bookmarks and opened pages, and upload device information to the attack’s command-and-control servers.
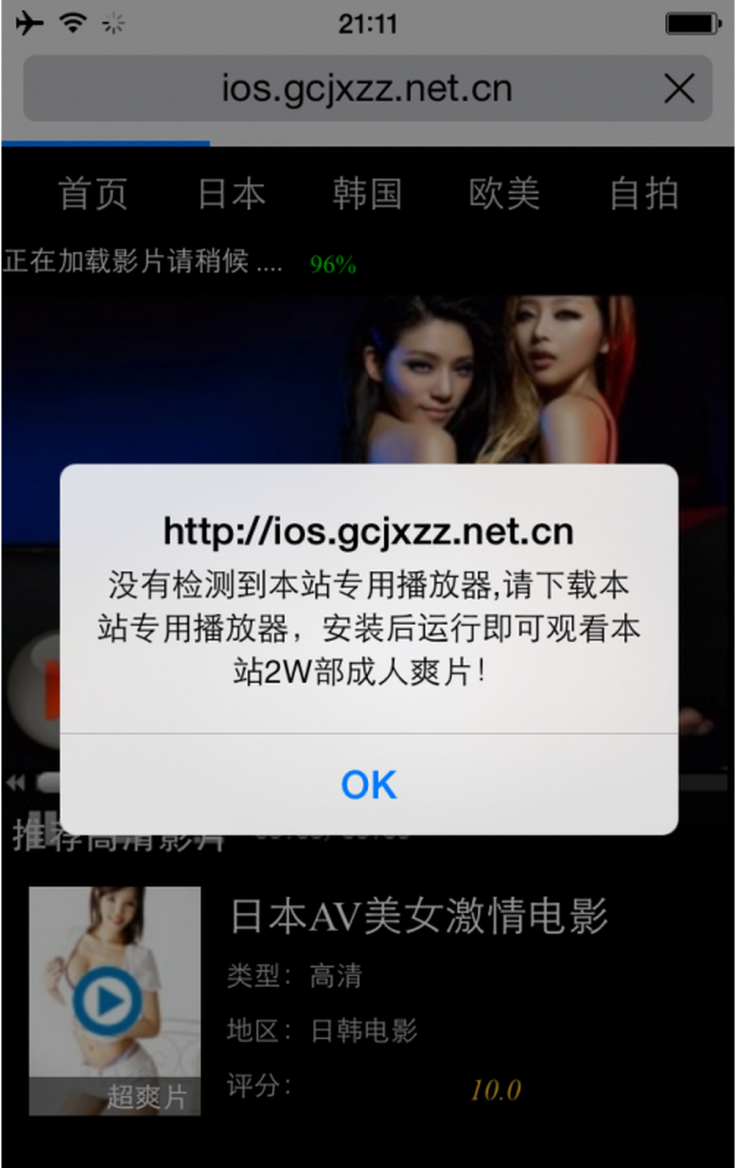
Xiao says YiSpecter was first spread in the wild in November 2014, though it could have been even earlier. To date 23 different versions of the malware have been uploaded to Virus Total, but just one of the 56 antivirus engines on the virus-checking service flagged YiSpecter as malware.
“The world where only jailbroken iOS devices were threatened by malware is a thing of the past. WireLurker proved that non-jailbroken iOS devices can also be infected through abuse of the enterprise distribution mechanism. YiSpecter further shows us that this technique is being used to infect many iOS devices in the wild,” Xiao said.
Once the main app is downloaded to a victim’s iPhone it silently downloads two additional apps which are able to disguise their presence on the device by remaining hidden on Springboard (the iOS desktop) while also disguising themselves as system apps such as Passbook and Game Center, tricking power users who pay closer attention to what’s happening on their devices.
Xiao says “there is a lot of evidence" that suggests YiSpecter was developed by a Chinese mobile advertisement platform and while there are some similarities between YiSpecter and XcodeGhost, the researcher doesn't believe they were developed by the same hackers.
Bypassing Apple's Security
The malware is able to bypass Apple’s typically strict code-review process by using three enterprise certificates which have been signed by Apple and belong to three different Chinese companies. This means the YiSpecter malware could be installed on non-jailbroken devices as an enterprise app.
Businesses typically install their own in-house apps using this method which bypasses Apple’s own app review process as the apps are not available through the App Store. When enterprise apps are installed, users get a pop-up notification telling them the name of the developer who created the app, but users typically just dismiss this without really taking notice of what it says. Apple has improved this system in the latest version of its software -- iOS 9 -- meaning users now must manually set a related provisioning profile as “trusted” in Settings before they can install the apps.
International Business Times has contacted Apple for comment but at the time of publication, it has not responded. This method of infecting iOS devices was previously used in the WireLurker malware campaign which also targeted iPhone and iPad users in China last year.
The attackers took advantage of the fact that a popular app for sharing porn videos called QVOD was terminated in April 2014 after its developers Kuaibo were investigated by the police in China. The main iOS apps of YiSpecter have user interface and functionality that enable the watching of free porn videos online, and were advertised as “private version” or “version 5.0” of QVOD.
Distribution
In order to afflict large numbers of iPhone users the attackers used four separate methods to spread their malware as widely as possible.
The first is by taking advantage of the fact that some Chinese ISPs hijack users’ internet traffic to display ads or send users to different webpages where promoted apps are automatically downloaded. In this case a pop-up dialog box appeared on popular news websites asking the users to install the fake QVOD app.
The malware was also spread using the instant messaging service QQ, developed by Tencent. Using a worm called Lingdun, the attackers were able to hijack a user’s account to spread files with names including pornographic and sexually suggestive words to all other QQ users in the same discussion group. If the files are clicked on, the malware will detect if the victim is using an Android or iOS devices and download the appropriate malware -- which in the case of iOS is YiSpecter.
The third attack method was spreading the YiSpecter malware on third-party app stores which are popular in China. The apps on these stores are not typically installed by end users but by mobile phone retailers and maintenance suppliers will install the apps (or in this case malware) on any phones they have physical access to in order to earn a commission from the app developer.
The final method to get the malware onto users smartphones was direct promotion on social networks and community forums.
© Copyright IBTimes 2024. All rights reserved.












