What Are Crypto Bridges?
You may have noticed that there are dozens of blockchain networks positioning themselves as key infrastructure for decentralized finance (DeFi) or play-to-earn (P2E) gaming. But what if none of the networks become big enough?
Can Web3 and DeFi achieve mainstream adoption with blockchain fragmentation? This is where blockchain bridges come in, as interoperability solutions between different blockchain networks. However, it is questionable if crypto bridges will ever be safe enough.
Dive in to understand the value of crypto bridges and the implications of their lower security.
What Are Crypto Bridges, and Why Do We Need Them?
Blockchain bridges are protocols that enable interoperability between different blockchain networks. As such, they enable the transfer of data (value) between two separate blockchain platforms, allowing them to communicate and interact with each other.
The purpose of a blockchain bridge is to provide a way for different blockchain networks to work together and exchange information, making it possible to use the combined capabilities of multiple networks for a wide range of decentralized applications (DApps).
For example, if you have large holdings of ETH from the Ethereum blockchain but you want to try out Avalanche (AVAX) because it is faster and cheaper, how would you go about it? You could use an exchange like Binance to convert some ETH portion into AVAX. You would then have Avalanche's native cryptocurrency.
But you could also use the Avalanche Bridge to transfer Ethereum's ERC-20 tokens to Avalanche and vice-versa. Although ETH itself is not an ERC-20 token, it can easily be wrapped as one in the form of wrapped ETH (WETH). One could manually convert ETH to WETH on any decentralized exchange like Uniswap, but the Avalanche Bridge automatically converts it to WETH.e to further differentiate it from regular WETH.
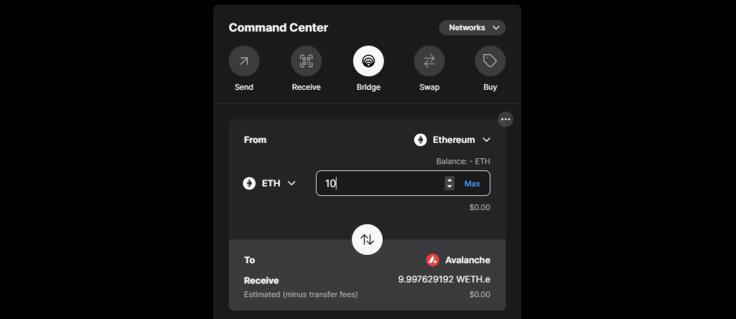
You would then connect your wallet to the Avalanche Bridge and transfer the funds to the Avalanche ecosystem, which can use ERC-20 tokens like WETH because Avalanche's C-Chain architecture is itself compatible with Ethereum Virtual Machine (EVM).
Other blockchains have similar interoperability solutions.
For instance, Solbridge is an EVM-compatible bridge between Ethereum and Solana. Even better, it connects Solana to Ethereum's Layer 2 scalability solution Polygon, enabling negligible gas fees and faster transactions. But what happens when a bridge is not EVM-compatible?
Let's first see how blockchain bridges work.
How Do Blockchain Bridges Work?
When we say "bridge," it evokes an image of a structure that hovers over ground/water to connect two pieces of land. In the digital world, such physical constraints and features don't exist. Therefore, it would be more precise to picture a blockchain bridge as a chamber.
Imagine two starships in space trying to connect with each other. Because of different pressures, they would need a connection through a pressurized chamber. This would allow the two ships to equalize the pressure between their respective interiors, ensuring that there is no sudden rush of air or other gasses when the connection is made.
By the same token, two blockchain networks need a chamber. Specifically, a token repository that uses smart contracts and communication protocols to facilitate an exchange of value. A smart contract, such as the one for the ERC-20 token, is a self-executing contract with the terms of the agreement between buyers and sellers being directly written into lines of code.
- A user deposits digital assets into the bridge's smart contract using the bridge's web interface.
- The smart contract locks those assets while issuing another token equal in value to the deposited funds.
- That newly issued token is then compatible with the other blockchain network's ecosystem of DApps.
Therefore, a blockchain bridge is an infrastructure that uses smart contracts and protocols to exchange value as an interoperability repository.
How Is a Blockchain Bridge Secured?
Each blockchain bridge has its own architecture. In general, though, just like nodes secure blockchain networks, nodes are responsible for validating transactions and maintaining a copy of the blockchain ledger on their local machines. Nodes are the individual devices that make up the network and run the blockchain software.
Validators are the entities that are responsible for validating transactions and adding them to the blockchain. In other words, node operators can host validators, although it is not a requirement. If node operators choose to run a node without hosting a validator, they will not participate in the process of adding transactions to the blockchain.
Case in point, following the North Korean hack worth $624 million on the Ronin bridge, which connects Ethereum to the Axie Infinity blockchain game, Sky Mavis increased the bridge's validator count to 17, with further increases pending.
1/
— Ronin (@Ronin_Network) August 17, 2022
We are thrilled to introduce three new Ronin network validators, bringing our total to 17, making progress towards achieving our initial goal of 21 independent validators collectively securing the network.$ron pic.twitter.com/BOfccYs86o
They did that because the Ronin bridge relied on just nine trusted and centralized validator nodes. This allowed hackers to use compromised private keys to break through the bridge's validator network, small as it was.
In contrast, the Ethereum network itself has more than 485,000 validators to secure the network. This is why decentralized bridges with higher node counts, just like blockchain networks, are deemed more trustworthy than centralized ones.
Types of Blockchain Bridges
Just like wallets, crypto bridges can be either custodial or non-custodial. Custodial bridges, just like centralized exchanges (Kraken, Coinbase), are centralized and trusted. Non-custodial bridges are decentralized and trustless.
For example, the world's largest exchange, Binance, has Binance Bridge on its BNB Chain. Although one could use that bridge via a Binance account, it is also possible to connect different networks through non-custodial bridges that are decentralized and trustless, such as Celer cBridge or AnySwap.
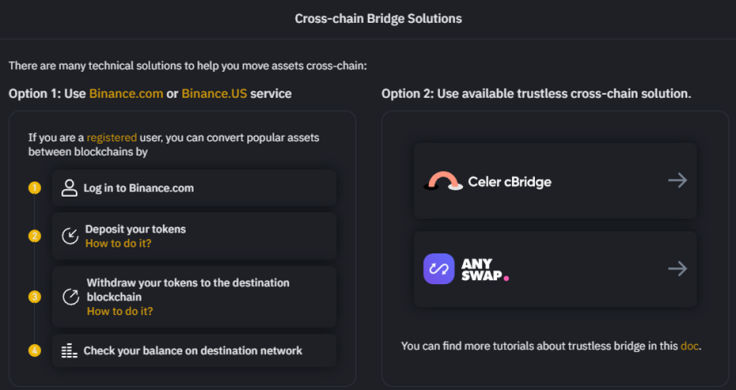
There are also uni-directional or bi-directional bridges. For example, the previously mentioned wrapping mechanism can be used to wrap Bitcoin as WBTC and use it on the Ethereum network as an ERC-20 token, but this is not possible in the other direction.
However, because Bitcoin is the largest cryptocurrency, WBTC uni-directional bridge has the largest total value locked (TVL) out of all crypto bridges.
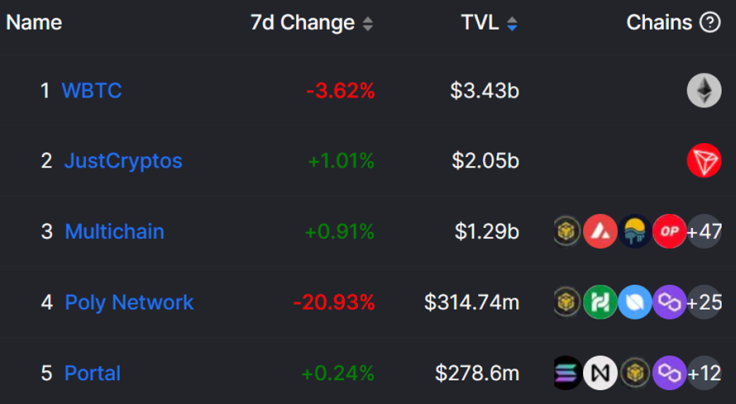
As you can see, blockchain bridges can hold more assets than entire blockchain networks. However, crypto bridges are highly controversial in terms of security.
Cross-Chain vs. Multi-Chain: The Difference From Bridge Vulnerability
It is no understatement to say that crypto bridges are the least secure cog of blockchain bridges. Because they serve as repositories, this makes them an exceedingly attractive target for hackers.
But also, as repositories, bridges tend to have drastically fewer nodes than their respective blockchain networks. Consequently, just in 2022, bridge hacks have resulted in $1.3 billion worth of damages.
This is almost half of all DeFi hacks in 2022. For this reason, Vitalik Buterin, the co-founder of Ethereum, made the case for there to be multi-chain operability instead of cross-chain operability. In other words, it would be safer to hold one's native assets on that specific network and convert them manually to another network's assets.
"It's always safer to hold Ethereum-native assets on Ethereum or Solana-native assets on Solana than it is to hold Ethereum-native assets on Solana or Solana-native assets on Ethereum."
Buterin further emphasized this importance in the scenario of 100s of blockchains. If one is successfully compromised, its native asset would then have inter-dependencies on other chains and DApps. For instance, if that chain's native token is used as collateral for a loan.
In such cross-chain codependency, the entire meta-blockchain economy would be at risk. In conclusion, one should view blockchain bridges as fundamentally insecure.
Nonetheless, one also has to account for layer 0 networks like Cosmos or Polkadot. With their relay/hub technology that connects different networks within a network, they circumvent the bridge's inherent flaws.

© Copyright IBTimes 2025. All rights reserved.





















