Kremlin-Linked Hackers Using Satellites To Hide Malware In US Government, Military and Research Institutions

A highly sophisticated cyberespionage group with reported ties to the Russian government is using satellites to remain hidden as it continues to attack systems in government, military and education institutions in the United States, China and the former Europe Bloc.
Also known as Snake or Uroburos, names linked to its highly advanced rootkit, the Turla cyberespionage group has been active for more than eight years and while attribution is difficult, there are multiple indications that link the group to Russia, including the language used in its malware and links to a cyberattack against the U.S. Department of Defense in 2008. Its victims are highly targeted and are located in government institutions, embassies, military, education, research and pharmaceutical companies.
By hiding communications in the Internet traffic of satellite providers, Turla has been able to hide its operations, and ensure that the command-and-control (C&C) servers used to communicate with, and control, infected systems remain online and out of the hands of the authorities.
Revealed by researchers at Kaspersky Lab, this innovative method is not unique among cyberespionage gangs, but the Turla group appears to be using it to make sure its highest profile targets remain infected.
Having infected a target’s system, the malware on the system sends a message to a decoy satellite Internet user. When that message is relayed by the satellite to the decoy user, the group takes advantage of the fact that satellite communication is unencrypted.
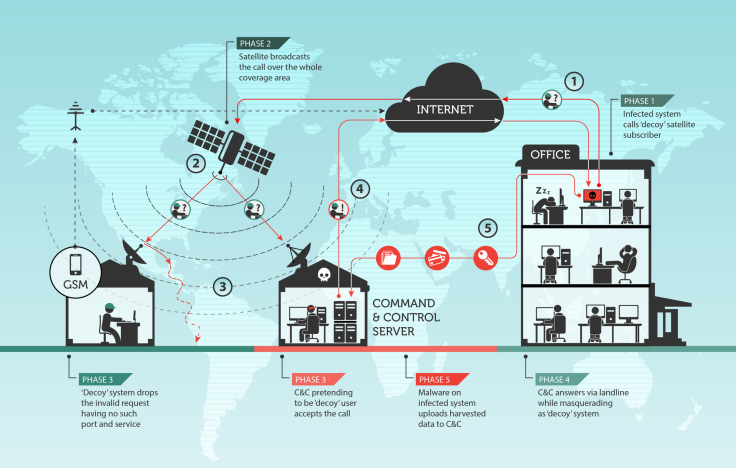
Using a satellite dish connected to the physical command-and-control servers, the hackers are able to pick up the message from the infected system, respond and eventually receive data it has harvested from the infected systems.
Staying Online At All Costs
Due to the highly sensitive nature of the targets that Turla has infected, this information is likely confidential and of interest to governments and hackers alike, and so the group is taking extra precautions to make sure its infrastructure is not knocked offline.
“The C&C servers are the central point of failure when it comes to cybercrime or espionage operations, so it’s very important for them to hide the physical location of the servers,” said Stefan Tanase, a security researcher with Kaspersky.
Turla is using satellite providers in Africa and the Middle East, and due to the range of coverage of these satellites, which can be up to 1,000 miles and span multiple countries or even continents, locating the physical command-and-control servers can be almost impossible.
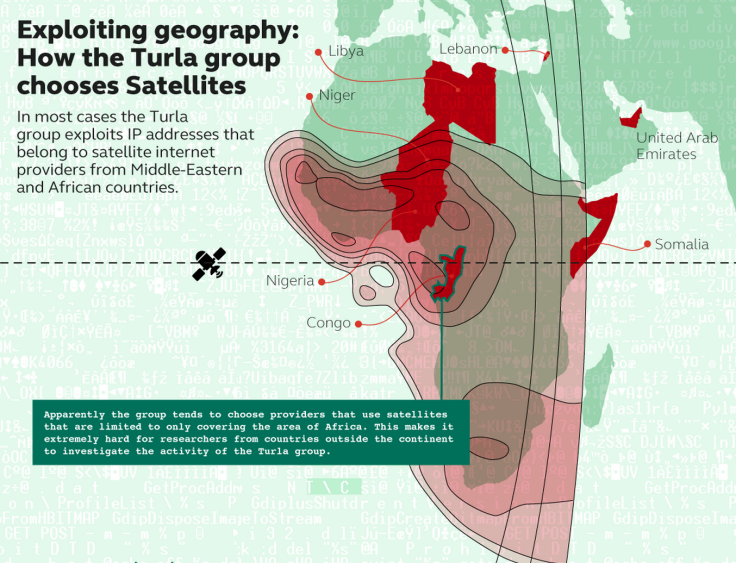
Kaspersky says that the only downside for the cybercriminals using this system is that satellite-based Internet is slow and can be unstable.
Bullet-Proof
Tanase added: "Considering how easy and cheap this method is, it is surprising that we have not seen more APT [advanced persistent threat] groups using it. Even though this method provides an unmatched level of anonymity, for logistical reasons it is more straightforward to rely on bullet-proof hosting, multiple proxy levels or hacked websites. In truth, the Turla group has been known to use all of these techniques, making it a very versatile, dynamic and flexible cyberespionage operation.”
While attribution in the world of cybersecurity is notoriously difficult, last year security researchers at Symantec published a report claiming that Turla was likely sponsored by the Kremlin.
Due to the highly sophisticated nature of the malware being used and the methods being deployed to remain on infected systems, it is almost certain that this group is sponsored by some government, and with the use of Russian language, as well as the targeting of Eastern Bloc countries, it is a safe bet to assume the Kremlin has some involvement in these actions — just as it is safe to assume the U.S. government is involved with the Equation Group that was uncovered earlier this year.
© Copyright IBTimes 2025. All rights reserved.





















