iOS 6.1.3 Released: The Evasi0n Untethered Jailbreak Killer Brings Fix For Passcode Unlock Bug, Improvements To Maps In Japan [Download Links]
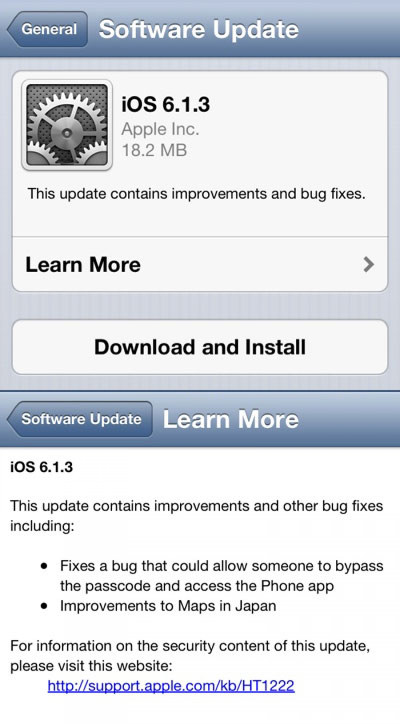
As expected before, Apple released the iOS 6.1.3 firmware update Tuesday for iPhone, iPad and iPod touch, bringing the fix for the widely reported passcode unlock bug that came to light recently.
Discovered over a month ago, the passcode unlock bug allows anyone to bypass the unlock feature on the Lock screen and thereby get immediate access to the user’s private stuff, including iMessages, FaceTime, photos and so on. However, with the release of iOS 6.1.3, Apple apparently brings the remedy for the anomaly.
Here’s how Apple has explained the fix for the passcode unlock bug:
Passcode Lock
Available for: iPhone 3GS and later, iPod touch (4th generation) and later, iPad 2 and later
Impact: A person with physical access to the device may be able to bypass the screen lock
Description: A logic issue existed in the handling of emergency calls from the lock screen. This issue was addressed through improved lock state management.
CVE-ID
CVE-2013-0980: Christopher Heffley of theMedium.ca,
videosdebarraquito
Apart from fixing the lock screen vulnerability, the new firmware update that takes the build number to 10B329 also comes with improvements to Maps in Japan. Here’s how the official change log of the update, weighing 18.2 MB, reads:
This update contains improvements and other bug fixes including:
• Fixes a bug that could allow someone to bypass the passcode and access the Phone app
• Improvements to Maps in Japan
As noted by a Redmond Pie report, the Japanese version of Apple Maps lacked some of the basic navigation features, which now have been added via the iOS 6.1.3 update.
In addition to “the implementation of turn-by-turn and better optimization of directions to favor highways over country lanes, Maps in Japan has also added a bunch of 3D landmarks,” said the report.
The latest improvements to Maps in Japan came on the heels of another set of update to the feature that Apple released last week. The company delivered a number of key fixes and improvements for its iOS Maps application in Japan through an over-the-air (OTA) update to non-iOS 6.1.3-beta devices.
If you want to update your device to the new firmware, go to Settings > General > Software Update to get it over-the-air. You can download it through iTunes and update the device after connecting it to your computer.
We’ve listed the supported devices below with direct links to the download files. What you have to do is just select the appropriate IPSW file for your device:
- iPad mini (GSM, CDMA, Wi-Fi)
Evasi0n Is Killed
With the release of the iOS 6.1.3, millions of jailbreak fans all around the globe will be anxious to know if the update has patched the exploits that made evasi0n possible. Well, it appears that the firmware update does bring an end to the iOS 6.x untethered jailbreak tool.
Well known iOS hacker MuscleNerd has confirmed via his Twitter account Monday that Apple has credited the evad3rs team for discovering four of the six security flaws, which have been fixed in the latest iOS 6.1.3 update. That said, if you want to save your current jailbreak, it’s highly recommended to stay away from the new firmware.
“Apple gives hat tip to @evad3rs for 4 of the 6 security fixes in 6.1.3 :) http://is.gd/nfspim,” MuscleNerd tweeted.
Apple has mentioned about one of the exploits in the security briefing as:
Kernel
Available for: iPhone 3GS and later, iPod touch (4th generation) and later, iPad 2 and later
Impact: A local user may be able to determine the address of structures in the kernel
Description: An information disclosure issue existed in the ARM prefetch abort handler. This issue was addressed by panicking if the prefetch abort handler is not being called from an abort context.
CVE-ID
CVE-2013-0978: evad3rs
In a recent interview with Forbes, renowned iOS hacker David Wang (aka Planetbeing) said that iOS 6.1.3 beta 2 included patches for at least one of the key exploits used by the hackers to create evasi0n. He was quite sure that having one exploit patched would have devastating consequences for future use of the evasi0n jailbreak tool.
However, the hacker also said that evad3rs had found out enough number of exploits inside Apple’s iOS platform to create a completely new jailbreak even if Apple manages to fix all the exploits that are currently being used. Considering that, it’s safe to believe that there will be a new jailbreak after all. But the only question is, when?
ALSO READ: Samsung Galaxy S4 To Miss Out On CyanogenMod Support? Don’t Lose Hope Yet, There’s More To It
© Copyright IBTimes 2025. All rights reserved.





















