Zuckerberg Hacked: Facebook Denies Reward To Palestinian Hacker, But Should Khalil Shreateh Be Paid For Discovering A Major Security Flaw?

A Palestinian hacker discovered a serious security flaw with Facebook that allows users to post to anyone’s Facebook Timeline, regardless of whether or not they're friends. The hacker, Khalil Shreateh, proved his point by posting directly to the private Facebook wall of Mark Zuckerberg. Unfortunately, Shreateh's method may have cost him at least a $500 reward.
Facebook claims that Shreateh violated the company's terms of service for its bounty program by exploiting a user’s Timeline (and Facebook's founder and CEO isn't just any user) to expose the bug. The decision has created a controversy in the hacker community. Some argue that Shreateh should have paid closer attention to Facebook’s rules; others argue this was the best way for the hacker to demonstrate the flaw and the damage he prevented outweighs a minor violation of Facebook's terms.

After discovering the bug, Shreateh posted to the Timeline of Sarah Goodin, a Harvard classmate and friend of Zuckerberg. Goodin's Facebook profile is private. He sent an email to Facebook’s security team with a link to the post.
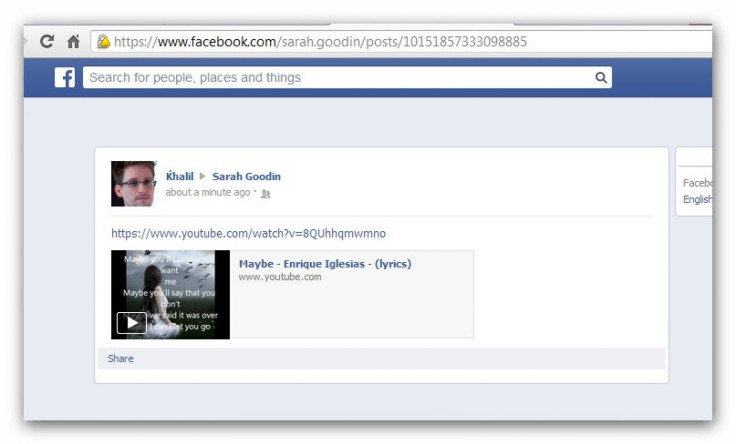
Facebook couldn’t see the post due to Goodin’s privacy settings and responded that the link only gave an error. Shreateh pointed this out, only to get a response that said, “Hi Khalil, I am sorry this is not a bug.”
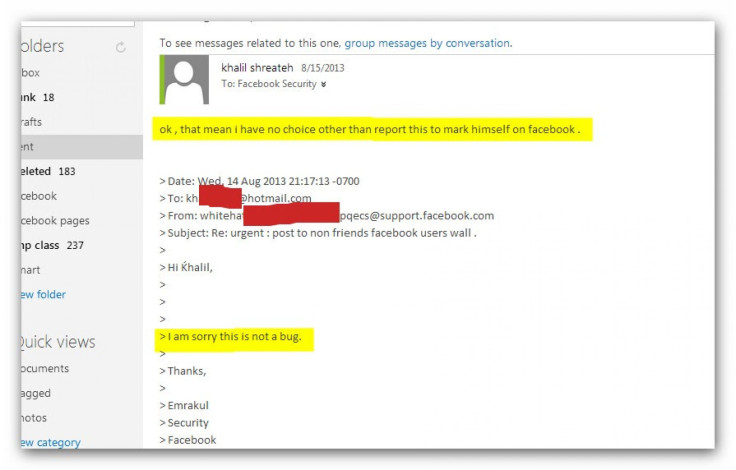
The hacker decided the only way he would get Facebook’s attention was to post directly to Zuckerberg’s wall, explaining how the security team was ignoring a pretty major vulnerability. Just imagine the damage malware spammers could do if given the ability to post on every Timeline on Facebook, regardless of a user’s privacy settings.
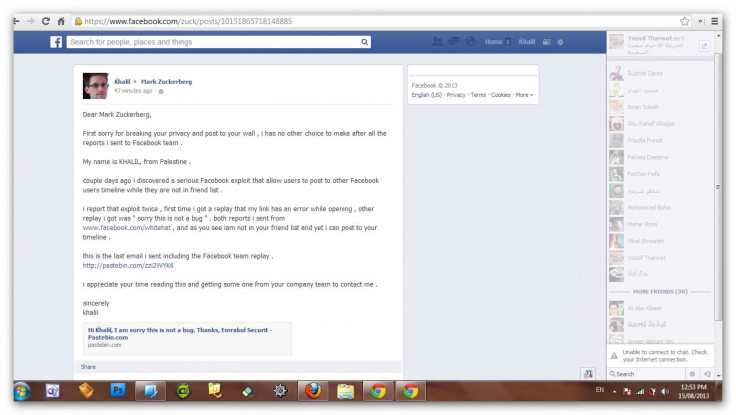
Within minutes of posting to Zuckerberg’s Timeline, a Facebook security engineer posted a comment asking for details on the exploit. Minutes later, Shreateh’s Facebook account was temporarily disabled. When the hacker asked why, he received the following response in addition to an explanation of why Facebook wouldn't pay him for his discovery.
Dear Khalil,
Facebook disabled your account as a precaution. When we discovered your activity we did not fully know what was happening. Unfortunately your report to our Whitehat system did not have enough technical information for us to take action on it. We cannot respond to reports which do not contain enough detail to allow us to reproduce an issue. When you submit reports in the future, we ask you to please include enough detail to repeat your actions.
We are unfortunately not able to pay you for this vulnerability because your actions violated our Terms of Service. We do hope, however, that you continue to work with us to find vulnerabilities in the site.
Like many tech companies, Facebook administers a “bounty program” that rewards benevolent hackers for uncovering bugs and security vulnerabilities. Facebook pays a minimum of $500 for legitimate bug reports, but it wouldn't pay Shreateh because he used another user’s profile without their permission.
Shreateh, however, has made his discovery public. The hacker posted a video to YouTube showing how he posted to a private Facebook Timeline without being friends with the user.
Should Shreateh be paid for his discovery? Does he deserve style points for proving his discovery on Zuckerberg's private Facebook profile? Let us know in the comments.
© Copyright IBTimes 2025. All rights reserved.






















