Symantec Discovers 'Regin', One Of The Most Powerful Computer Viruses Ever Built
Symantec said Monday it uncovered a piece of malware propagating around the world that's used for spying on Internet service and telecommunications companies. The virus, which has been dubbed "Regin," is of unknown origin, but researchers at the security company say the malware's construction is sophisticated enough that it may have come from hackers backed by a nation-state.
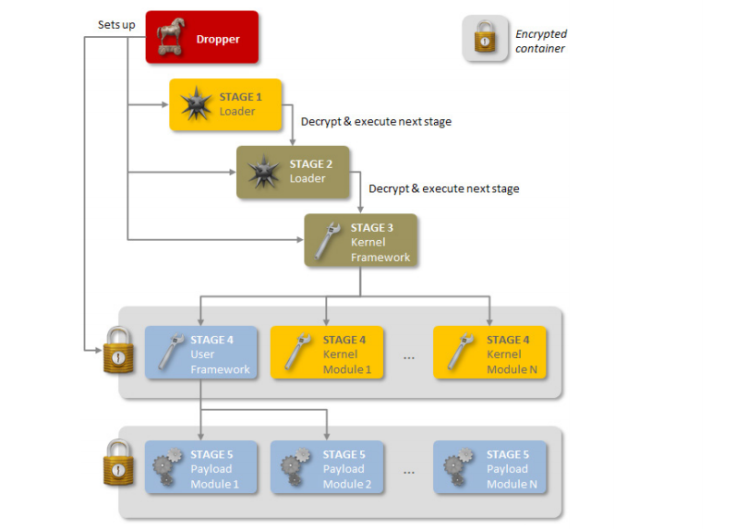
Symantec released a 21-page white paper on its findings, outlining Regin as a "complex piece of malware whose structure displays a degree of technical competence rarely seen," with an "extensive range of capabilities" that grants operators "a powerful framework for mass surveillance."
"Regin is highly customizable and could be used for a variety of things," said Orla Cox, Symantec security operations manager. By swapping out the malware's payload, a hacker can change its abilities. It's akin to pulling the appropriate tool from a Swiss Army knife to change the purpose of the entire object. "We wanted to gather as many of these payloads as possible to see what it's capable of," said Cox.
One such payload is a classic standby for black-hat hackers — a remote access tool, or RAT, that lets attackers control a victim's computer from afar, copy files, and even turn on a webcam. One of its more intimidating payloads lets it spy on GSM networks. A spokesperson for Kaspersky Labs said that means Regin can access "information about which calls are processed by a particular cell, redirect these calls to other cells, activate neighbor cells and perform other maliciously offensive activities like conceivably shut down the GSM cellular network."
Given the high-level nature of the software, Symantec's Cox said that the skills necessary to develop something of this scope could come only from the work of a full-time team over months or years, working to test and improve it. "This is at the high end of malicious code and requires a lot of skill," she said. "If you look at what they're stealing — the infrastructure of mobile phone networks and mobile telecom companies — it's a large amount of data. In order to be able to filter it and do something with it, that itself requires a large amount of resources."
Kevin Johnson, CEO of SecureIdeas, hypothesized that this is not the work of a government but rather a moneymaking scheme for those responsible for developing it. "This is really interesting malware from an attacker perspective. I look at it and go 'That’s awesome,'" he said. "This is a really cool framework that’s being built so you can buy it and load it with malware of your choice. Symantec just advertised how great this malware is and raised its value."
Regin targets systems running Microsoft's Windows operating system. Approximately 100 Regin infections have been detected so far. A combined 52 percent of these are in Russia and Saudi Arabia, and the rest are spread throughout Mexico, Ireland, India, Afghanistan, Iran, Belgium, Austria and Pakistan. Regin's country of origin is unknown, but Re/code pegs the shortlist for suspects in the United States, Israel and China.
© Copyright IBTimes 2025. All rights reserved.





















