Solving the Puzzle of Security in Web3 for Continued Future Success
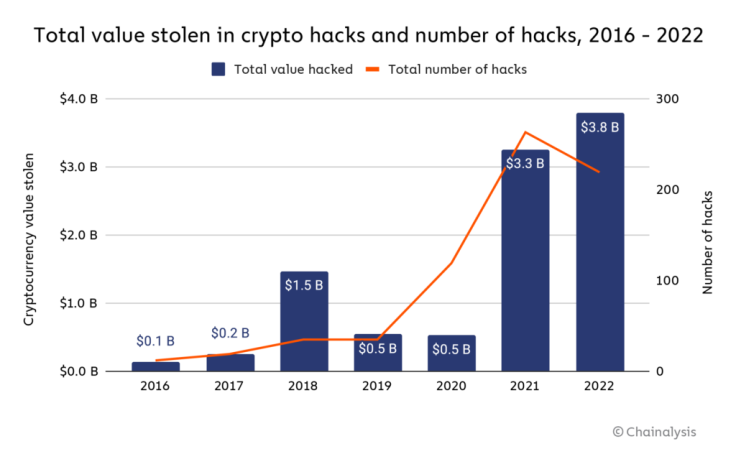
Over the past year alone, we have witnessed hacks and platform compromises that have amounted to billions of dollars. To put things into statistical context, all through 2022, $3.8 billion worth of assets were stolen from cryptocurrency businesses, making 2022 the biggest year ever for crypto hacking. This trend is especially alarming and could have been prevented with the right security measures.
Unfortunately, the Web3 sector, in its present iteration, is quite limited when it comes to the security side of things, putting the technology's future evolution and viability in jeopardy. Therefore, moving ahead, we must solve this conundrum to pave the way for Web3's continued success. I sat down with David Schwed, COO of cybersecurity firm Halborn, to learn more about the current state of Web3 security.
Why security matters?
It is no secret that Web3 promises a decentralized and trustless environment where individuals have full control of their digital assets. In other words, it is a new era of the internet with enormous potential; however, it does come with its fair share of risks, mainly due to the lack of centralized control. The very essence of Web3, which is decentralization, makes it difficult to secure platforms, leaving them vulnerable to attacks from multiple vectors, including smart contracts, wallets, and nodes.
As a result, mitigating/solving Web3's existing security needs is critical because it can make or break the technology. In fact, if we don't address these security challenges, we may witness a decline in adoption, and the technology may never reach its full potential. Fortunately, there are several cybersecurity solutions that can help us solve the security puzzle in Web3.
Security practices that can help Web3 become more secure
Comprehensive Security Assessments
Security practices must encompass a wide range of services to ensure the best protection for Web3. These services can include Security Architecture Assessment, Code Audits, Custom Red Team Engagements, Web Application /Cloud Provider/API Pen-Testing, and Continuous Smart Contract Auditing, among others. By employing a comprehensive approach, organizations can identify and address potential vulnerabilities at every level of their infrastructure. In this regard, David Schwed, COO of blockchain security firm Halborn, believes:
"An integral component of a secure Web3 ecosystem lies in security assessments. By examining every aspect of an organization's infrastructure, it is possible to identify potential vulnerabilities and provide actionable insights to protect their digital assets. Halborn's approach combines various service packages, ensuring a holistic perspective that covers all aspects of security."
Advanced Penetration Assessments
To keep up with the ever-evolving threat landscape, advanced penetration assessments are crucial. This involves deep security inspection and the latest offensive security tactics to uncover critical vulnerabilities before they are exploited. By conducting penetration tests on web apps, wallets, layer 1 blockchains, and more, organizations can safeguard their digital assets against potential attacks.
Regular Smart Contract Audits
Smart contract audits can help make Web3 systems more secure by identifying and addressing potential security vulnerabilities — such as logical flaws, incorrect or missing input validation, etc — in their code before they are deployed for public utilization. They can also help in:
- Preventing attacks: Smart contract audits can help prevent attacks on the contract and the blockchain network, such as denial-of-service attacks, reentrancy attacks, and other malicious attacks. By identifying and addressing vulnerabilities, developers can make it harder for attackers to exploit the code and compromise the security of the network.
- Ensuring compliance: Smart contract audits can ensure that the contract complies with regulatory requirements, such as anti-money laundering (AML) and know-your-customer (KYC) regulations, by verifying that the code follows the relevant guidelines and standards.
Halborn specializes in providing a thorough analysis of blockchain applications' smart contracts to correct design issues, errors in the code, or identify security vulnerabilities, ensuring the smart contract application or DeFi platform is ready for mainnet deployment.
DevOps and Automation
Incorporating security into the development process is essential for a secure Web3 ecosystem. By automating security and development processes, organizations can save time and money. Practices such as automated scanning, CI/CD Pipeline development, Infrastructure as Code, and Cloud Deployment can help build an effective DevSecOps culture that prioritizes security throughout the development lifecycle.
Speaking about the role of DevOps and automation within the framework of a secure Web3 ecosystem, Schwed noted: "Integrating security into the development process is a fundamental aspect of building a secure Web3 ecosystem. By incorporating security best practices and continuously refining development processes, organizations can streamline their operations while prioritizing security at every stage."
Continuous Security Improvements
Security maintenance is an ongoing process, and organizations must constantly adapt and evolve to stay ahead of emerging threats. Continuous improvement practices include Web App Pen Testing, Cloudflare Configuration, Smart Contract Auditing, Mobile App Pen Testing, and Cloud Auditing/Configuration, among others. By implementing a dynamic security optimization process, organizations can maintain a strong security posture and protect their digital assets.
Collaboration and Security Advisory-as-a-Service (SAAAS)
Dedicated support from security engineering specialists and effective communication are vital for successful security implementation. Having a dedicated account manager and a project management dashboard can facilitate client approvals and ensure all parties are aligned on the project's progress. Public or private reports generated as needed can also help organizations make informed decisions about their security strategies.
By offering continuous assessment and world-class cybersecurity consulting, SAAAS can help organizations stay ahead of the curve and maintain robust security practices in a rapidly evolving tech landscape.
Looking ahead
Web3 is a promising technology that can revolutionize the digital paradigm as we know it. However, its vulnerability to security breaches necessitates solving the puzzle before the technology can be adopted more widely. Fortunately, there are several cybersecurity solutions that can help us achieve this. With the right security measures in place, we can unlock the full potential of Web3 and build a decentralized and trustless environment where individuals have full control of their digital assets.





















