CryptoLocker Virus Infects 12,000 Computers In One Week: How Hackers Are Avoiding Detection

Bitdefender Labs, an American and Romanian anti-virus company, found that in the week beginning Oct. 27, more than 12,000 computers were infected with the CryptoLocker virus, a malware capable of holding the contents of a hard drive for ransom. Bitdefender also noted that the hackers behind CryptoLocker seem to be exclusively targeting computers in the U.S.
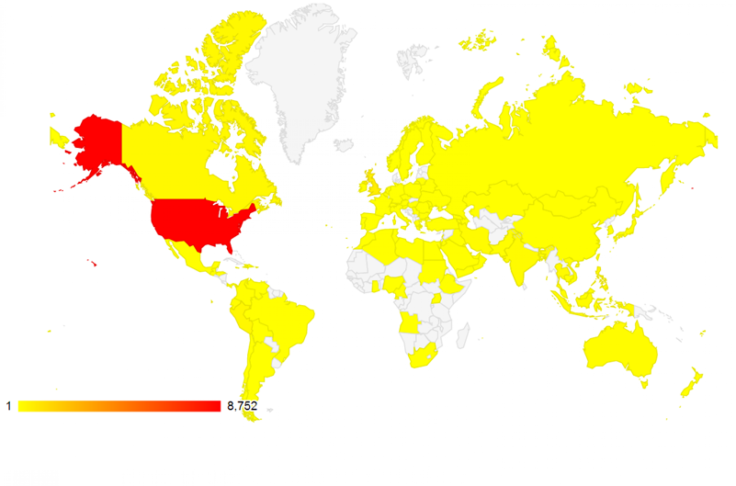
The CryptoLocker hackers use an algorithm to generate new command and control subdomains every day, making it difficult to track down the criminal hackers.
Bitdefender reverse-engineered this domain generation algorithm and sinkholed the relevant domain names, which allowed Bitdefender to register the CryptoLocker domains before they disappeared.
Between Oct. 27 and Nov. 1, 12,016 hosts infected with CryptoLocker contacted the sinkholed domains. So many came from IP addresses in the U.S. that Bitdefender concluded that infections in other countries are simply collateral damage of an attack aimed there.
To further hide their tracks, the CryptoLocker hackers are frequently changing the servers that host the CryptoLocker virus. Bitdefender told IB Times that it’s rare for CryptoLocker to remain on the same server for more than a week. In the week Bitdefender monitored, Cryptolocker servers were identified in Russia, Germany, Kazakhstan and the Ukraine.
Unfortunately, this constant “server hopping” is only going to make it more difficult to catch the criminal hackers.
The CryptoLocker virus is spread through phony FedEx and UPS tracking notifications, as well as emails pretending to come from other legitimate businesses. One the malicious link is opened, the malware scans a harddrive for documents, spreadsheets, photos and more before encrypting them. CryptoLocker then launches a pop-up window with a counting down clock. If a $300 ransom is not paid in Bitcoin before the time expires, the decryption key is deleted and the user may never regain access to their files.
Recently, the CryptoLocker hackers began offering a second chance to claim the decryption key, but the ransom is five times that of the original ransom.
Security experts are working on anti-decryption software than can guard against the CryptoLocker virus. In the meantime, they advise users to remain vigilant regarding links they open and to not give into demands if infected with CryptoLocker.
© Copyright IBTimes 2025. All rights reserved.






















